
“Bee” a Responsible Defender against smish and vish
As a Responsible Defender, learn how to detect and report a text and voice phish.
Companies have seen a significant uptick in phishing threats that go “beyond email”—primarily smishing and vishing through text messages and phone calls. While the names of these attacks might be fun to say, the impact they can have is incredibly serious. Let’s take a closer look at these two trending concerns and how you can continue to enable and protect our organization as a Responsible Defender.
What are smish and vish?
A smish is a phishing attack carried out over text messaging.
A vish is a phishing attack carried out over a phone call or voicemail.
Senders or callers pretend to be trusted parties and attempt to gain sensitive information like login, passwords, financial account details and more.
Similar to email phishing, your best defense against both smishing and vishing is to think before you act. If something doesn’t seem or feel quite right, it probably isn’t. Look for these clues to help you identity smish and vish:
Five ways to identify smish and vish
When in doubt, always verify the request through a trusted source, like the official website, email or phone number you’ve used before for your contact.
Keep in mind that vendor and executive impersonation is on the rise. This is an example of an actual smish with an attacker impersonating the CEO.
As a Responsible Defender, you know how to report suspicious emails using the Report Phish button in the Outlook toolbar. For smish and vish, there’s another button.
How to report smish and vish
For employees in most countries, go to the bottom of the “Quick Links” section on the homepage and click the Cybersecurity Concerns button. For all other teams, please follow your local phish reporting procedures.
One
Two
Three
Five
Four























Hi Stephen
let me know if you
are available. There is something I need you to do and also your confidentiality would be appreciated. Reply me here once you get this.
Thanks. Tom CEO
The text or call is unexpected and urgent, asking for immediate action—click a link, open an attachment or provide personal information.





The text or call is ambiguous, lacking details about the urgent request.


You’re asked to keep the request confidential and not to tell anyone else.


The text or call is
not how the known contact would
typically communicate with you.


You don’t recognize
the phone number of the text or call.









An example of smish in action
Cybersecurity Concerns
Emergency Information
Technology
Help Hub
Compliance Helpline


An example of smish in action
When in doubt, always verify the request through a trusted source, like the official website, email or phone number you’ve used before for your contact.
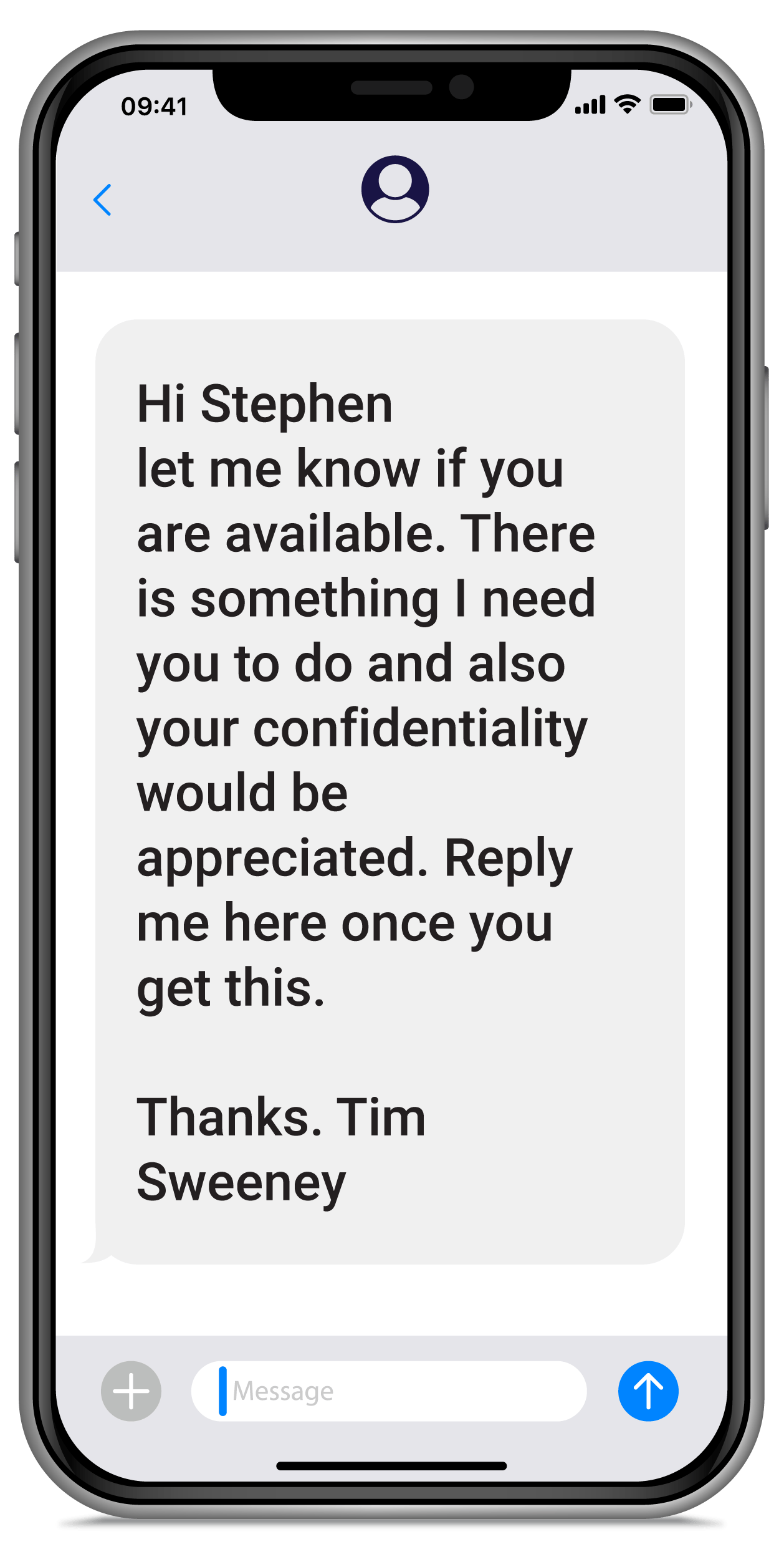
Keep in mind, Liberty Mutual vendor and executive impersonation is on the rise. This is an example of an actual smish with an attacker impersonating CEO Tim Sweeney.


Hi Stephen
let me know if you
are available. There is something I need you to do and also your confidentiality would be appreciated. Reply me here once you get this.
Thanks. Tim Sweeney
Canvas quiz height: 3132
Canvas no quiz height: 2497

Internal use only
Not active
Close
I developed this page using the Ceros platform and graphics from a designer.